TYPES OF CABLE
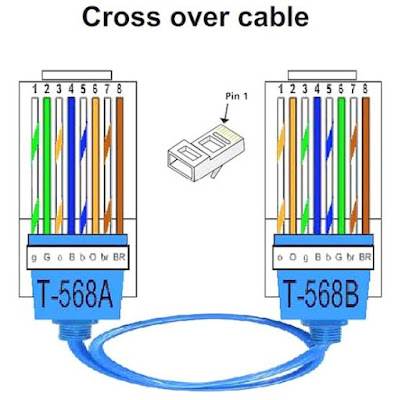
1. Twisted-pair cable
- Is the most common type of cable.
- Have eight individual copper wires bundled together and covered with an insulating material.
- The copper wire is always color-coded with a plastic insulation and they are twisted in pairs for a total of four pairs.
a. STP (Shielded Twisted Pair)
- Often used in “noisy” environments where a shield of metallic foil is wrapped around each of the wire pairs, with an additional overall shielding to protect against excessive electromagnetic interference.
b. UTP (Unshielded Twisted Pair)
- Is the most common form of twisted pair wiring. It is less expensive and easier to work with than STP.
.
2. Coaxial Cable
- the standard media used by cable TV operators.
- it consists of a plastic insulator that separates the solid copper inner conductor and the woven, copper braid outer conductor.
3. Fiber-optic Cable
- has a reflective coating that allows light beams to travel without outer interference.