NETWORK TOPOLOGY
There are two types of network topologies: physical and logical.
Physical Topology emphasizes the physical layout of the connected devices and nodes, while the Logical Topology focuses on the pattern of data transfer between network nodes.
TYPES OF TOPOLOGY

Bus topology is a network type in which every computer and network device is connected to single cable.In networking a bus is the central cable -- the main wire -- that connects all devices on a local-area network (LAN). It is also called the backbone. This is often used to describe the main network connections composing the Internet. Bus networks are relatively inexpensive and easy to install for small networks. Ethernet systems use a bus topology. When it has exactly two endpoints, then it is called Linear Bus topology.
Advantages of Bus Topology
- It is cost effective.
- Cable required is least compared to other network topology.
- Used in small networks.
- It is easy to understand.
- Easy to expand joining two cables together.
Disadvantages of Bus Topology
- Cables fails then whole network fails.
- If network traffic is heavy or nodes are more the performance of the network decreases.
- Cable has a limited length.
- It is slower than the ring topology.
RING TOPOLOGY

A local-area network (LAN) whose topology is a ring. That is, all of the nodes are connected in a closed loop. Messages travel around the ring, with each node reading those messages addressed to it.
Advantages of Ring Topology
- Transmitting network is not affected by high traffic or by adding more nodes, as only the nodes having tokens can transmit data.
- Cheap to install and expand
Disadvantages of Ring Topology
- Troubleshooting is difficult in ring topology.
- Adding or deleting the computers disturbs the network activity.
- Failure of one computer disturbs the whole network.
STAR TOPOLOGY


All the nodes in the network are connected to a central device like a hub or switch via cables. Failure of individual nodes or cables does not necessarily create downtime in the network but the failure of a central device can. This topology is the most preferred and popular model.
Advantages of Star Topology
- Fast performance with few nodes and low network traffic.
- Hub can be upgraded easily.
- Easy to troubleshoot.
- Easy to setup and modify.
- Only that node is affected which has failed, rest of the nodes can work smoothly.
Disadvantages of Star Topology
- Cost of installation is high.
- Expensive to use.
- If the hub fails then the whole network is stopped because all the nodes depend on the hub.
- Performance is based on the hub that is it depends on its capacity
MESH TOPOLOGY
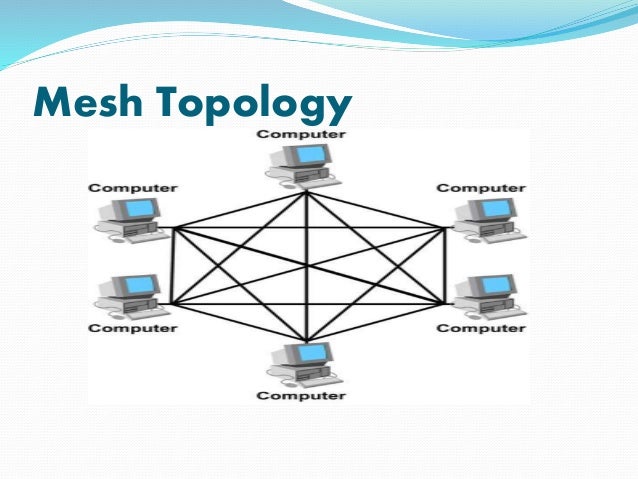
The topology in each node is directly connected to some or all the other nodes present in the network. This redundancy makes the network highly fault tolerant but the escalated costs may limit this topology to highly critical networks.It is a point-to-point connection to other nodes or devices.
There are two techniques to transmit data over the Mesh topology, they are :
- Routing
- Flooding
MESH Topology: Routing
In routing, the nodes have a routing logic, as per the network requirements. Like routing logic to direct the data to reach the destination using the shortest distance. Or, routing logic which has information about the broken links, and it avoids those node etc. We can even have routing logic, to re-configure the failed nodes.
MESH Topology: Flooding
In flooding, the same data is transmitted to all the network nodes, hence no routing logic is required. The network is robust, and the its very unlikely to lose the data. But it leads to unwanted load over the network.
Advantages of Mesh Topology
- Each connection can carry its own data load.
- It is robust.
- Fault is diagnosed easily.
- Provides security and privacy.
Disadvantages of Mesh Topology
- Installation and configuration is difficult.
- Cabling cost is more.
- Bulk wiring is required.
HYBRID TOPOLOGY

It is two different types of topologies which is a mixture of two or more topologies. For example if in an office in one department ring topology is used and in another star topology is used, connecting these topologies will result in Hybrid Topology (ring topology and star topology).
Advantages of Hybrid Topology
- Reliable as Error detecting and trouble shooting is easy.
- Effective.
- Scalable as size can be increased easily.
- Flexible.
Disadvantages of Hybrid Topology
- Complex in design.
- Costly.